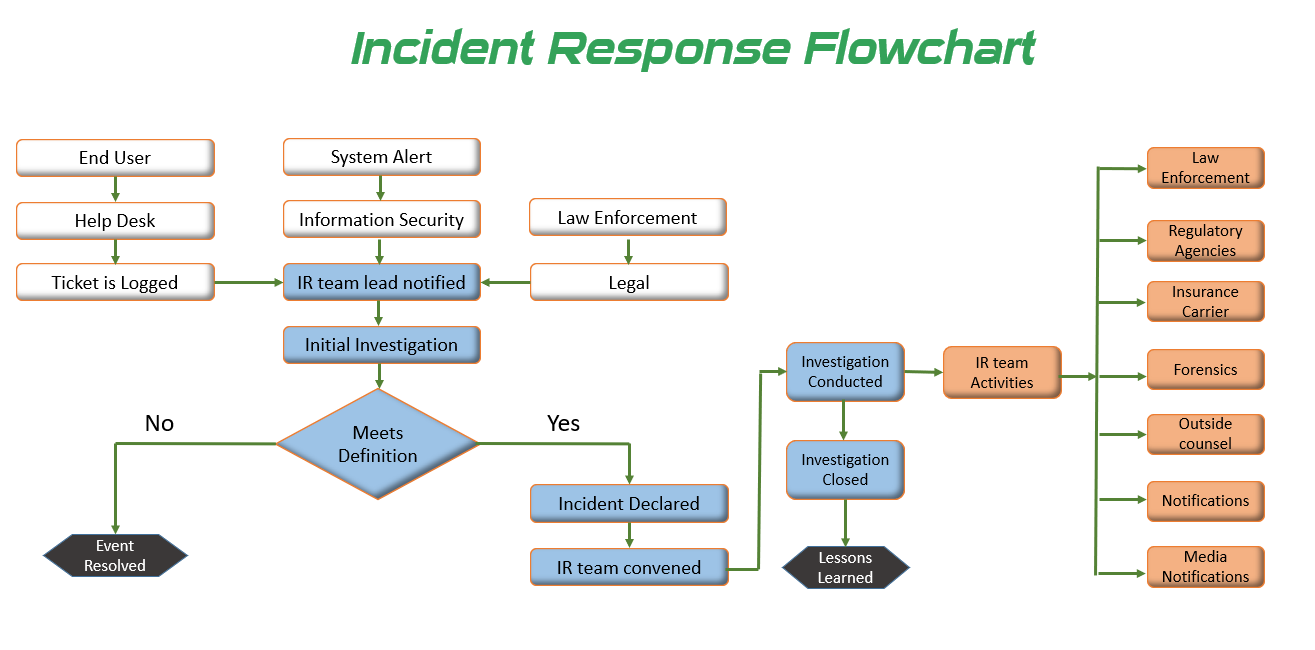
In today’s digital landscape, cybersecurity incidents have become a common occurrence. To effectively respond to such incidents, organizations need to have a well-defined cybersecurity plan in place. Here are the steps you need to go through when enacting a cybersecurity plan during an incident:
1. Identify and Assess:
The first step is to identify the incident and assess its severity. This involves gathering information about the incident, understanding the potential impact on the organization’s systems and data, and determining the scope of the incident.
2. Activate the Incident Response Team:
Once the incident is identified, activate the incident response team. This team should consist of individuals with expertise in cybersecurity, IT, legal, and communications. They will be responsible for coordinating the response efforts.
3. Contain and Isolate:
The next step is to contain and isolate the incident to prevent further damage. This may involve disconnecting affected systems from the network, disabling compromised accounts, or isolating infected devices.
4. Investigate and Analyze:
Conduct a thorough investigation to understand the root cause of the incident. Analyze the evidence, logs, and any other relevant data to determine the extent of the breach and the methods used by the attacker.
5. Mitigate and Remediate:
Develop a plan to mitigate the impact of the incident and remediate the vulnerabilities that led to the breach. This may involve patching systems, updating security controls, or implementing additional security measures.
6. Communicate and Report:
Keep stakeholders informed about the incident, its impact, and the steps taken to mitigate it. This includes notifying affected individuals, regulatory bodies, and law enforcement agencies, if necessary.
7. Learn and Improve:
After the incident is resolved, conduct a post-incident review to identify lessons learned and areas for improvement. Update the cybersecurity plan based on these findings to enhance the organization’s preparedness for future incidents.
By following these steps, organizations can effectively enact their cybersecurity plan during an incident, minimizing the impact and protecting their systems and data. Remember, preparedness and a swift response are key to mitigating the risks associated with cybersecurity incidents.